Managing Third-party Remote Access for Mine Site’s
Background
When managing 100s of third party users, mine sites need to ensure that they are providing safe and secure access to their critical operational technology systems with just enough access for the vendor and third party to service the technology system within their network environment.
This becomes increasingly challenging as access methods are unsuitable for operational technology security, and is neither sustainable or scalable for the mine site across their vendors and third parties, making it difficult manage, monitor and control the network securely.
Provide third parties granular remote access to systems and applications
Direct Application Access
Dull provides the speed and simplicity for users to connect directly to the application, without comprising users experience or blocking traffic to the selected application.Connections isolated from the corporate network
Dull enables users to connect directly to the application without seeing any other systems within the corporate network. This helps maintain a strong security posture when providing access to internal and third parties users.Invisible Application Access
Dull allows users to access applications without directly connecting to the targeted network. This creates an invisible connection between the user and the application, acting as a 'darknet'. This keeps the infrastructure invisible, reducing the risk of exposing the corporate network, while the user accesses the application to complete their task.Multi-Factor Authentication (MFA)
Dull operates on the principle of least-privileged access, making MFA a large part of authenticating the user's identity to access applications. Multi-Factor Authentication (MFA) forces third party users to verify their identity before accessing critical operational technology systems within the mine sites network.Visibility and Control
Dull centralises control of all users and their assigned applications, enabling organisations to see the entire network activity of their users, user groups, third party suppliers in real-time. Making it easy to manage all users and their access across many different network environments, therefore reducing risk by increasing visibility, auditability, and control.Granular remote access hidden from other systems and applications
Secure Collaboration
Provide each organisation with independent sovereign accounts
Uniquely with the Dull Platform, organisations can securely create and manage remote access with other Dull Platform users. This empowers each organisations to manage and maintain their assets within their part of the network whilst being able to collaborate securely in a controlled and standardised manner. This creates stronger collaboration, security, control and transparency of who access what and when.Isolate third-party users to approved devices, systems and applications
When using the Dull Platform, third party users are provided access to individual applications specific systems they have been approved to. When accessing these systems at any given time, third party technicians are only able to see the application they have access. This isolates third party technicians to an application-level view without exposing them to the entire corporate network.Control who accesses what and when within your part of the network
The Dull Platform enables organisations to maintain granular control who accesses what and when within their part of the network. When collaborating with third parties, this becomes critical to ensure that only approved users are accessing approved systems aligned with their role-base privileges.Standardised access across all organisations
Instead of operating and maintaining different access methods and products across multiple organisations. Dull standardises remote access by maintaining one way of connecting across all organisations and third parties.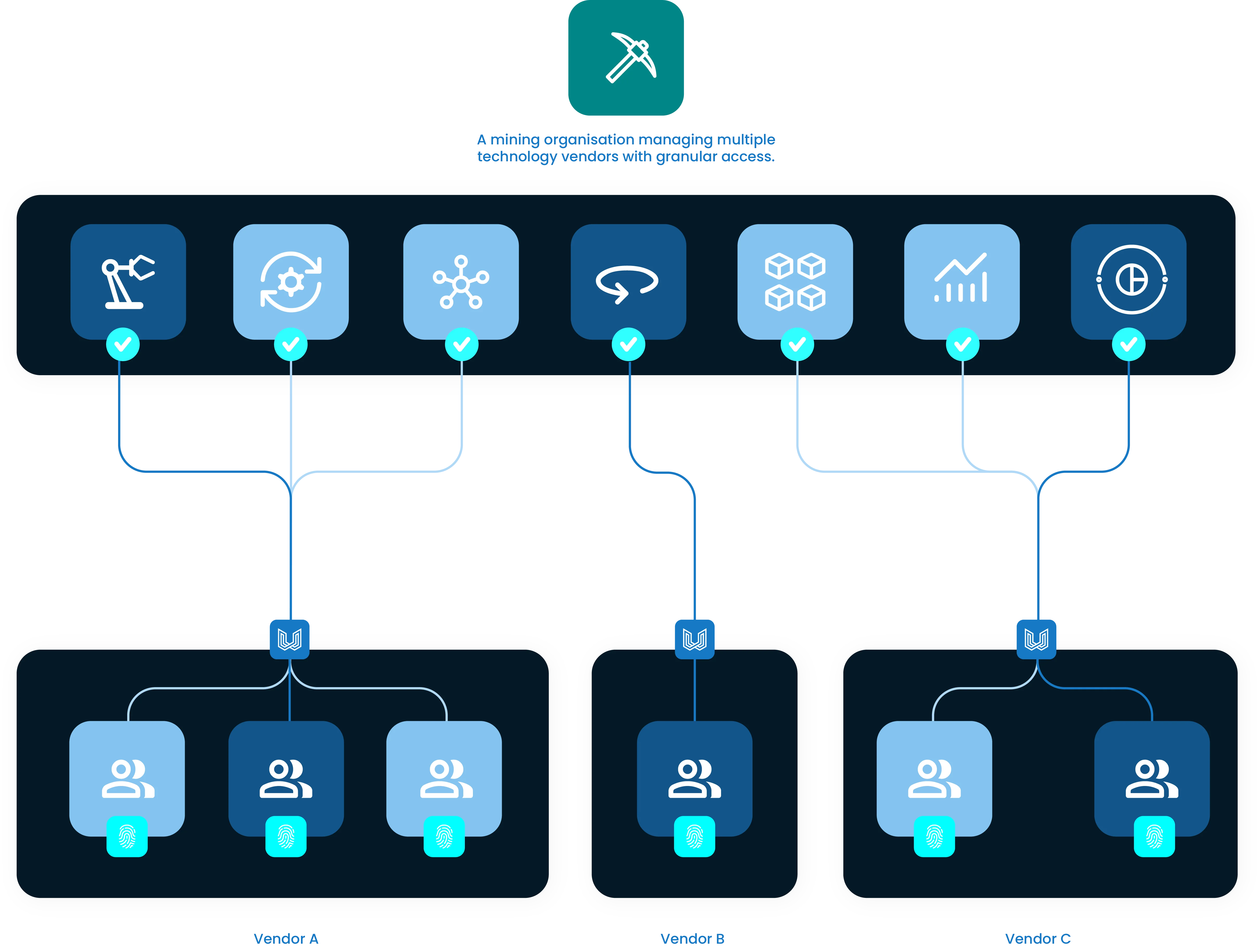


Talk to an expert
Secure remote access to managed devices, systems and applications