Defence
Securing and encrypting communications to and between mission critical systems.

The Challenges with Remote Access in OT environments
IT-centric remote access tools & solutions were never not built to ensure the security, integrity, and continuity of OT environments.
Whilst these products provide access to these networks and their devices, the underlying network security, configuration, and control falls short, leaving our most sensitive devices and applications vulnerable to threat actors.
- Shared accounts and device credentials
- Lateral movement
- Single-factor authentication
- Overly permissive network access
- No remote access visibility
- Minimal remote access controls
- No documentation of who accessed what
- Complex firewall and network management
The limitations of these solutions can include:
- Shared accounts and device credentials
- Lateral movement
- Single-factor authentication
- Overly permissive network access
- No remote access visibility
- Minimal remote access controls
- No documentation of who accessed what
- Complex firewall and network management

How secure is your Remote Access Solution?
- Rely on VPNs and Jumpboxes to provide users remote access to the engineering workstation.
- Provide third party users (OEMs) too much access with little control of users within the OT network.
- Are unable to lock down users to individual devices or applications running within the OT network.
- Lack the visibility & auditability of who accessed what and when.
- Isolates & microsegments employees and third parties to individual services or applications running within the IT/OT network.
- Establishes just-in-time mTLS network connections to that are provisioned on the fly and torn down after each connection.
- Securely logs all remote connections with the ability to jump in and watch a live connection.
- Provides secure and flexible configuration to suit any TCP/IP protocol or legacy device.
Securing high-value targets with Dull
The Dull Platform is a software-defined & cloud-delivered solution designed to secure employees, OEMs, third parties, and contractors with application-level remote access across complex supply chains, remote locations, and legacy infrastructure with Zero Trust Security approach.
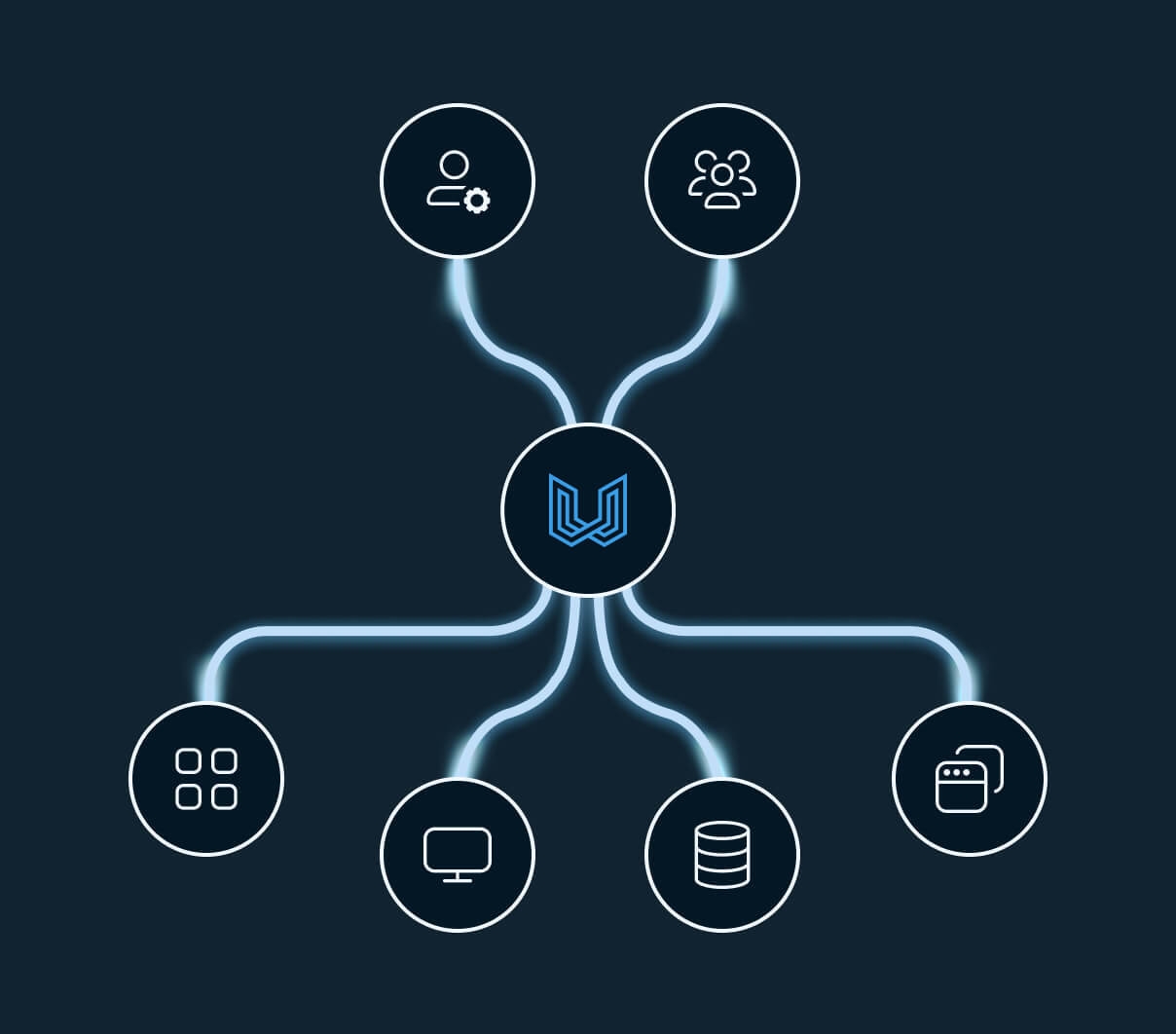
- Lockdown any user, access and asset to as an individual remote connection.
- Establish granular and multi-layered access control to any modern or legacy asset.
- Have visibility and control of all remote connections with detailed connection logs.
- Simplify and consolidate remote access management with one platform.
- Microsegment every remote connection to abolish lateral movement.
Secure and empower your organisation with Dull

Zero Trust Security with Secure Microsegmentation
Isolate and lockdown remote access to individual devices and applications.
Third parties
Employees
OEM's
Contractors
Satellites
Vessels
Facilities
Office
Aero
A secure & efficient solution for
defence
Isolated Remote Access
Lockdown remote access sessions to an individual device, service or application with end-to-end encryption and just-in-time network access.
Multi-layered MFA
Enforcing multi-factor authentication on users, devices and critical services running on site, by adding layered MFA across mission critical services.
Moving Target Defense
Randomise the IP address and Port number for each remote connection, making it impossible to predict what IP and Port number will be used to connect to the destination service.
Ephemeral Virtual Machines
Provision remote access to fully isolated and non-persistent virtual machines that enable the operational environment to meet the precisive operational requirements of a customer.
Session Recording
Capture the full remote access session within a secure and non-invasive operating system locked down to the particular device, service or application.
Session Shadowing
Jump into any live remote access session and observe every interaction the users are performing to the destination service with the ability to terminate active session.
Secure Credential Launching
Centrally manage your IT/OT devices and applications without revealing the username or password to the end user.
Full Connection Logs
Understanding who was accessing what and when with detailed session logging of the user's initiating device, MFA device, IP address, the PID, subsequent network session, admin authentication and more.
SOC/NOC Integrations
Use Dull a part of your security operations to build a comprehensive approach to analyse, detect and response to any cyber security incident.


Talk to an expert
Secure remote access to managed devices, systems and applications