A Cyber Attack waiting to happen - VPN's provide too much access
Are Virtual Private Networks suitable for operational technology environments?
Over the last decade, VPNs have worked well to secure the confidentiality of remote user's access to the client or corporate network. However, over the previous few years there has been a paradigm shift towards remote work. Through this change, worker patterns have evolved from working one-two days at home to three-four days.
The change in worker patterns matched with digital transformation has accelerated the pressure to secure critical remote operations from rapidly increasing cyber threats. Organizations have been using IT tools to secure their operational technology systems, which puts OT systems at risk.
Operational technology systems can't be managed with traditional IT tools as they require different security protocols and access control in order for these systems to be securely accessed internally and externally by third-parties and business partners. These systems are mission-critical to large organisations, and support multi-million and billion-dollar operations that require security and continuity on a 24/7 basis.
How can VPNs cause a supply chain risk?
Where is the value in changing to an OT-native remote access tool?
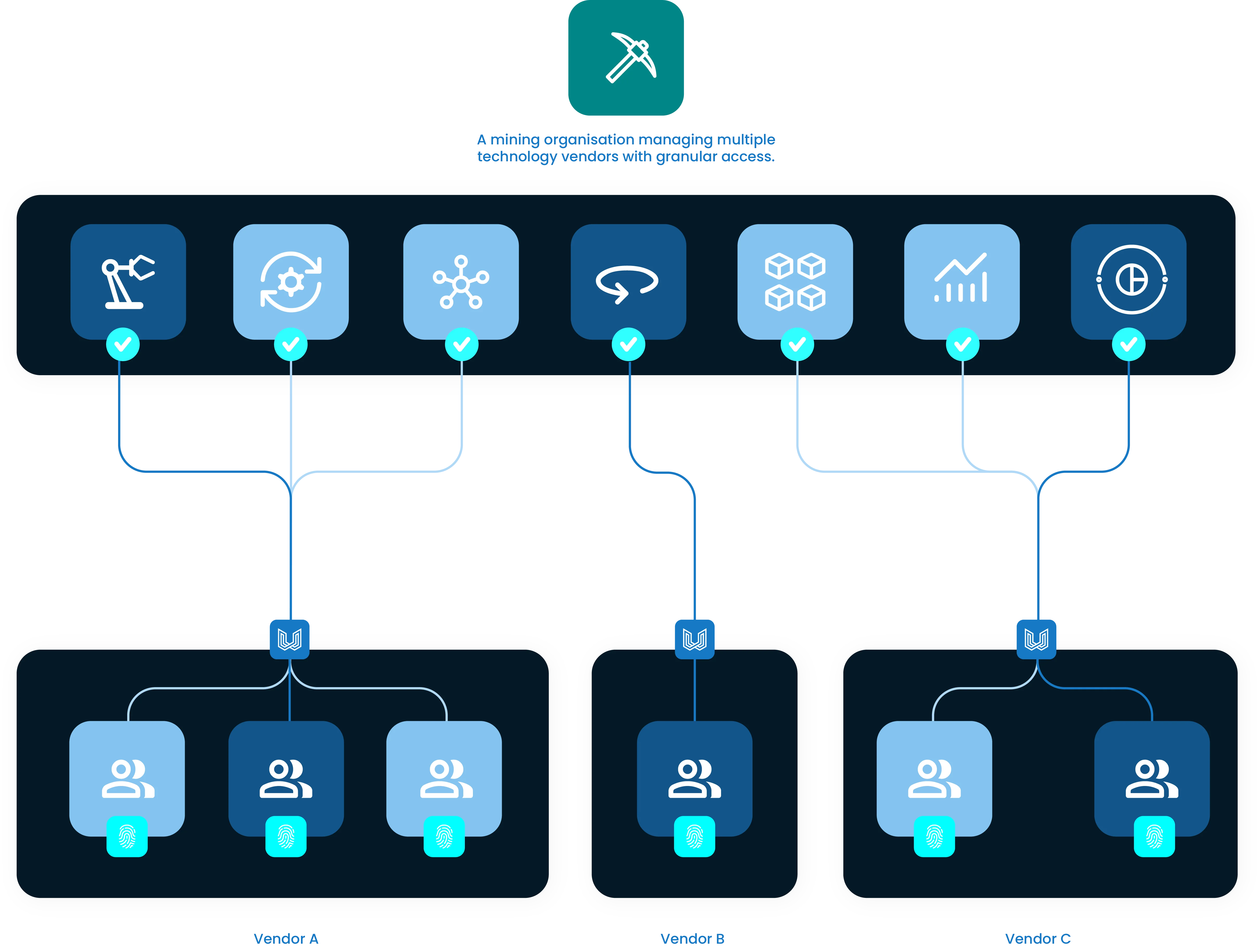
Secure Remote Access solutions like Dull are focused explicitly on OT & ICS systems and applications, securing more than just the confidentially of communications but increasing the security through granularity and obscurity. Together, this helps ensure the availability and continuity of operating systems.
Using an OT-native secure remote access tool like Dull, organisations can:
Isolate multiple organisations and users to individual applications


Talk to an expert
Secure remote access to managed devices, systems and applications